Network Sniffing and Security Measures
Network Sniffing in Detail and Security Measures
Sniffing is a common word in everyday parlance. However, does it have any alternative usage in the realm of Cybersecurity? How about using Network Sniffing as a cybersecurity jargon? Currently, most of the people that are already a part of the field are aware about the concept of Sniffing. However, for an average Internet user, it may be a foreign term. However, let us attempt to understand what it really is, right from scratch.
It is the most commonly used trick, you can say or science or a mechanism(whatever suits you) used by prying hackers. It involves the following:
- Capturing
- Identifying
- Decoding
- Inspecting
- Interpreting
Now, for those who don’t know, packets are the lifeline of internet communication. They are the messengers that carry information. Like in old days if somebody could catch a pigeon that carried a note, they would get to read it. It is like that pigeon. But network sniffing is not catching the pigeon, it is just being able to read what it is carrying.
Anyway coming back, the purpose of this network sniffing can be anything from spying to serious attack planning, hacking credit card details or trying to understand the behavior of the target. Most widely it is used to acquire authentication credentials. To understand what the packet contains in depth, we should know what is the OSI Model. It is a standard followed by the TCP/IP protocol abiding by which packets are generated at one end and received and decoded at the other. They are the rules of communication and essentially are divided into layers.
#Network #Sniffing and #Security Measures: https://t.co/ThRXBnGNhf#infosec #cyberspace #wifi #theCBI
— The Cyber Blog India (@incyberblog) February 16, 2016
That is why they say, if you are connected, You are vulnerable.
Even if your packets are well encrypted, anyone on the network sitting silently can map out your entire topography and carry out another attack like the more sophisticated Man in the middle.
Network Sniffing can either be done internally when someone is sitting on your network or on your firewall that sends packets outside or even wireless by catching packets that your transmitters send in the air. Network sniffing is a constructive activity at times also, when it is used to analyse and troubleshoot networks but most significantly it is used by hackers.
A packet is like a free bird meant to reach somewhere but it does not mean that it cannot be stored or made a copy of. A sniffer software contains its own network driver and buffer memory in order to capture a large chunk of packets. More elite sniffers are capable of analyzing the packets and converting them into more statistical data.
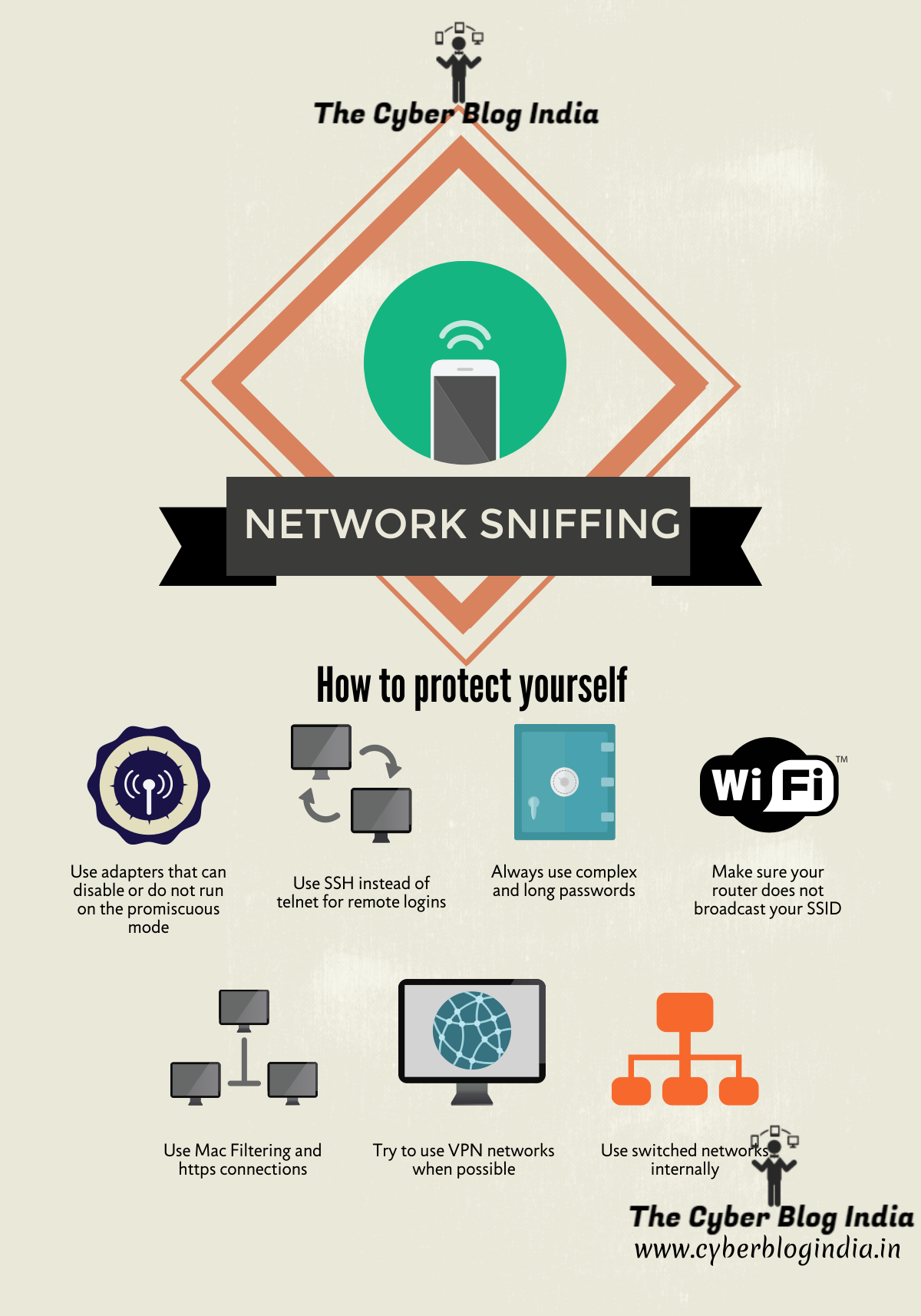
So how to protect yourself Talking about protection,
- First thing is to possibly turn your adapter to disable the promiscuous mode(if your adapter allows, else change it) But there is no certainty of this application.
- Use SSH instead of telnet to remote log in.
- Always have more complex and long passwords to your routers.
- Make sure that your router is not set to broadcast your SSID. This will stop sniffers like Net Stumbler.
- Use Mac filtering. Most of the latest routers support this.
- Always try to login to https connections only.
- Try to use VPN services when using free public WiFi.
- The safer but not so convenient way is to use switched networks. Switched networks are designed to deliver packets directly to the node and are not visible to other nodes decreasing the chances of sniffing it on the way. Also it is easy for administrators to detect sniffers on switched networks. There are some anti sniffing tools available on the internet like XArp, Arpwatch, Wireshark etc. but then they are all limited to a level.

