Save Your Sensitive Information From Malicious INSIDERS!
A sensitive information is always at a threat from outside hackers, and we’ve employed a number of methods and tools to prevent it. But there are people sitting inside the organization too, who pose a threat to this information. These people are called ‘insiders.’ An insider threat, according to WhatIs, is a malicious hacker who is an employee or officer of a business, institution, or agency. The term can also apply to an outside person who poses as an employee or officer by obtaining false credentials. The hacker obtains access to the computer systems or networks of the enterprise, and then conducts activities intended to cause harm to the enterprise.
Following are a few suggestions you should apply in order to avoid attacks from inside to a great extent.
- Monitor, Discover, and Protect: Know where your most important, and confidential data is stored. Always keep a check on this data. This might be a tricky job, as large organizations tend to have scattered and large databases which are quite difficult to track.
- Segregate and Mask: Segregation of data according to the employees’ needs is the smartest move one can apply to ensure security from within. Employees must be given access to the data they need, and usage of this data must be monitored. Real time masking is also a method to avoid a breach. Masking is technique in which all the information is not visible to one viewing it, thus barring the viewer from accessing the entire data. This can be achieved by using a dynamic data masking tool.
- Use Multi-Layered Technique: A multi-layered technique like using a two-factor authentication tool, or bio-metric tools along with a password or pin can be employed in order to ensure extra security. This will keep a track of ‘who’ is accessing ‘what,’ and thus monitoring will be easy.
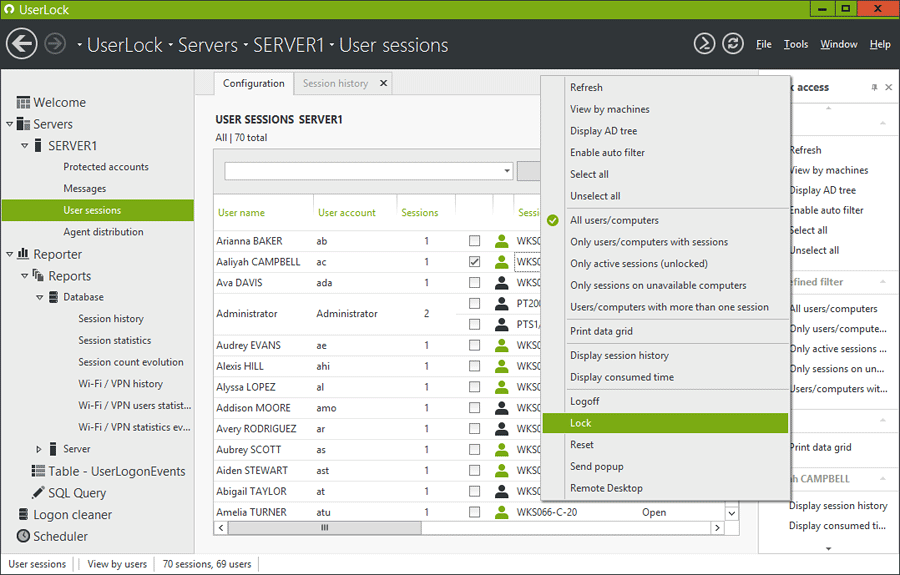
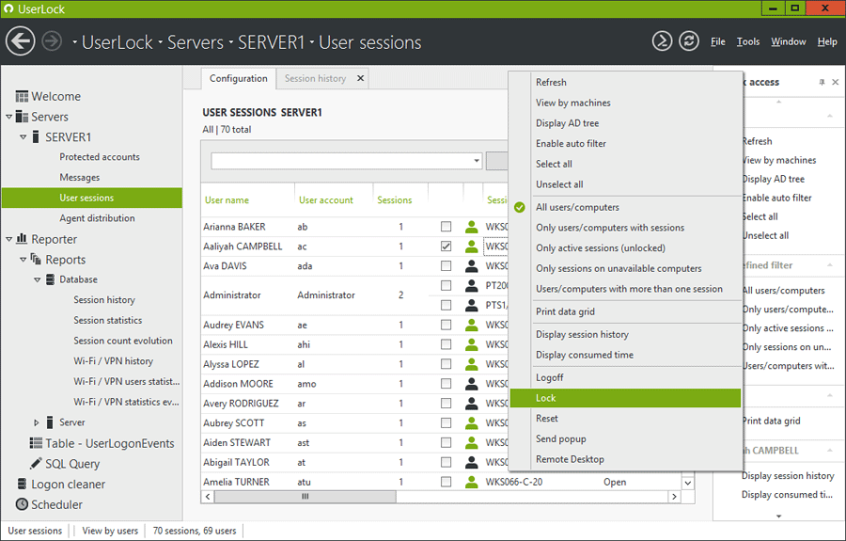
- Use Security Tools: There are a lots of tools that will help you monitor your important information, like FileAudit and UserLock. UserLock by ISDecisions is a tool that’s widely because of its easy-to-use interface and functionality. It does the following things for you:
- Stops unauthorized access, especially when the password credential is compromised.
- Doesn’t allow password sharing by preventing concurrent logins.
- Immediate response to suspicious behavior
- Remote locks and masks on user’s sight
The following video depicts how this tool may be helpful to your organization: